SSH Key Management: Best Practices & Security Guide
Are your digital fortresses truly secure? Failing to properly manage Secure Shell (SSH) keys is akin to leaving the back door unlocked in your IT infrastructure, inviting potential cyberattacks and compromising sensitive data. This is no longer a matter of best practice; it's a fundamental necessity in today's threat landscape.
Understanding and implementing robust SSH key management is paramount for safeguarding your systems and networks. This crucial aspect of cybersecurity extends beyond mere convenience; it's the cornerstone of secure remote access, streamlined workflows, and regulatory compliance. From generating and protecting keys to rotating and backing them up, the intricacies of SSH key management, when mastered, offer a significant boost to your overall security posture. Ignoring these best practices, however, can expose your organization to a range of risks, including unauthorized access, data breaches, and severe compliance penalties.
In today's complex IT environments, SSH key management has become a multifaceted challenge. Unlike their counterparts, SSL/TLS certificates, SSH keys lack an expiration date by default. This fundamental difference leads to the exponential growth of keys across an organization over time. It is estimated that a large corporation such as a Fortune 500 enterprise may have close to a million SSH keys in use. This volume, combined with the inherent complexities of distributed systems and diverse user roles, creates a significant management burden.
- Movierulz Risks Understanding Alternatives Legal Ways To Watch Movies
- Secure Remote Iot P2p On Windows 10 Free Guide Setup
Heres a closer look at the core principles and key considerations involved in SSH key management:
| Category | Details |
|---|---|
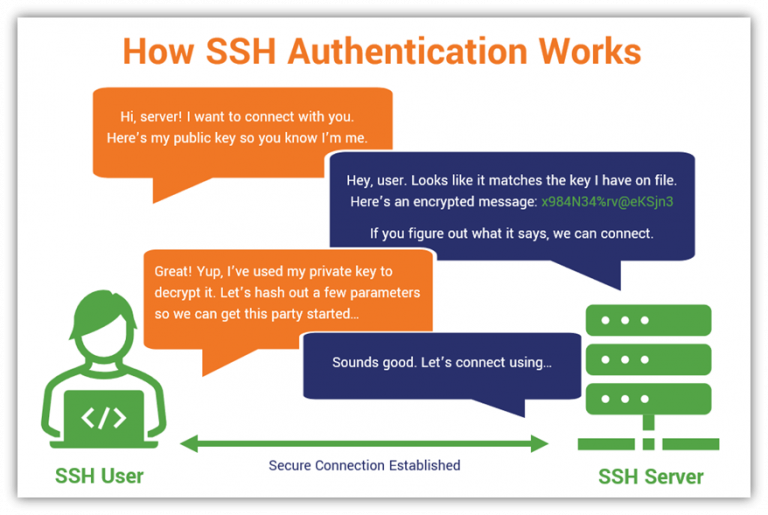
| Key Generation | The process of creating SSH keys. This involves generating a public-private key pair, with the private key remaining confidential and the public key deployed on remote servers. The security of the private key is paramount. Use strong, modern cryptographic algorithms such as Ed25519 or RSA with a key length of at least 2048 bits. |
| Protection | Securing the private keys is the cornerstone of SSH key management. Employ robust measures such as password-protecting private keys and storing them securely. Consider utilizing hardware security modules (HSMs) or secure enclaves for added protection. |
| Rotation | Regularly rotating SSH keys is a fundamental security practice. Rotate keys periodically to limit the impact of potential key compromises. Establish a clear schedule for key rotation, typically every 90 to 180 days, depending on the sensitivity of the systems being accessed. |
| Backup and Recovery | Implement a reliable backup and recovery strategy to ensure business continuity. Regularly back up SSH keys and ensure they are stored securely and separately from the original keys. Have a well-defined procedure for key recovery in case of key loss or compromise. |
| Key Revocation | Establish a system to revoke compromised or unnecessary keys promptly. This prevents unauthorized access. Upon a key compromise or when a users access is terminated, promptly revoke their associated SSH key. |
| Access Control | Implement strong access controls to regulate who can use specific SSH keys. Restrict SSH key usage based on roles, responsibilities, and least privilege principles. Regularly review and update access controls as needed. |
| Monitoring and Auditing | Continuously monitor and audit SSH key usage. Implement monitoring tools to detect unusual activity, such as unauthorized login attempts or unusual key usage patterns. Regularly review audit logs to identify potential security incidents or policy violations. |
Centralizing and automating SSH key lifecycle management is a crucial step in enhancing security and efficiency. Organizations often face a decentralized and complex landscape of key management. This typically leads to significant manual effort and increased risk of errors. By centralizing the entire key lifecycle, organizations can ensure consistent application of security policies and streamline management tasks.
Consider the following best practices for centralized management:
- Utilize a dedicated SSH key management tool: A centralized tool, like Keeper Secrets Manager or similar, streamlines key storage, access control, and automation.
- Automate key provisioning and revocation: Automation minimizes human error and ensures swift response to security events.
- Implement role-based access control (RBAC): RBAC restricts key access based on user roles and responsibilities, significantly reducing the risk of unauthorized access.
Automation plays a crucial role in efficient SSH key management. Automating key rotation, provisioning, and revocation significantly reduces the administrative overhead and minimizes the potential for human error. Moreover, automation allows security teams to respond rapidly to security incidents and enforce security policies consistently. These aspects collectively bolster the organization's security posture. Automation of the key lifecycle reduces manual intervention, which is a major cause of security incidents. Automated processes can quickly identify and address suspicious activity.
The benefits of a well-managed SSH key infrastructure are numerous and significant. First and foremost, it enhances security by mitigating risks associated with compromised credentials and unauthorized access. It improves operational efficiency by streamlining key management tasks and reducing administrative overhead. Furthermore, it supports regulatory compliance by ensuring adherence to security standards and best practices. Effective SSH key management translates to a more robust and resilient security posture, enabling organizations to focus on core business objectives.
Conversely, unmanaged or poorly managed SSH keys can expose organizations to substantial risks and inefficiencies. The risks include unauthorized access, data breaches, and regulatory non-compliance. Ineffective management leads to operational inefficiencies, such as difficulties in key tracking, rotation, and revocation. It also increases the likelihood of failed audits and significant regulatory penalties. Prioritizing SSH key management is, therefore, a vital step in safeguarding the organization's security and maintaining business continuity.
Key Management Challenges
Managing SSH keys presents several challenges for organizations, making it a complex undertaking. Here's a breakdown:
- Lack of Expiration Dates: Unlike SSL/TLS certificates, SSH keys lack a built-in expiration mechanism, leading to key accumulation over time.
- Key Proliferation: The decentralized nature of SSH often leads to the uncontrolled creation and distribution of keys across an organization.
- Manual Processes: Many organizations rely on manual processes for key management, such as tracking keys via spreadsheets or documenting them manually. This can be time-consuming, error-prone, and inefficient.
- Visibility and Control: Gaining full visibility and control over SSH key usage across an organization is often difficult, making it challenging to identify and address security vulnerabilities.
- Decentralized Management: Many organizations lack a centralized system for SSH key management, which results in inconsistent security practices and fragmented processes.
- Integration and Automation: Integrating SSH key management with existing IT infrastructure and automating key lifecycle processes can be complex and time-consuming.
- Compliance Requirements: Meeting compliance requirements, such as those mandated by industry regulations, necessitates robust SSH key management practices.
A significant evolution in SSH key management involves adopting keyless SSH access, which simplifies security administration and lowers the risk of key-based attacks. Keyless access means you're still using SSH protocol, but instead of managing permanent keys, you utilize a zero-trust framework with dynamic credentials. This approach greatly reduces the management overhead and potential for security breaches by eliminating long-term key storage.
Passwordless access, in conjunction with keyless access, provides a potent strategy for eliminating the risk of compromised access credentials and authentication keys. This combination strengthens security by eliminating static keys and passwords, which are common targets for attackers. By focusing on a zero-trust model, organizations can dramatically improve their security posture.
Various tools and services facilitate robust SSH key management. The choice of tool will depend on your organizations specific needs and infrastructure. Some popular options include:
AWS Key Management Service (KMS): A managed service that facilitates the creation and management of cryptographic keys used for data protection. It provides centralized control, auditing, and key rotation capabilities, integrated with other AWS services. This is good for users who have infrastructures on AWS cloud.
PrivX Key Manager: This key manager offers a zero-trust approach to SSH access. It centralizes key management, simplifies access control, and automates key processes like provisioning and rotation. It also integrates with various systems, enhancing overall security.
Keeper Secrets Manager: This tool securely stores and protects your SSH keys, along with other IT infrastructure secrets. It integrates with existing build systems to create dynamic, programmatic access to your secrets.
Thales Key Management Offerings: These offerings provide a streamlined approach to key management in cloud and enterprise environments. They offer robust security features, including centralized key management, encryption, and access control. This is good for the organizations, especially with a diverse use case.
Openssh Certificates: OpenSSH certificates provide a way to issue short-lived, signed certificates. This mitigates the need to manage individual keys on a per-user basis. It allows for the centralization of the authentication process. They are extremely helpful in situations where ephemeral access is needed.
These tools provide options for creating, securing, and managing SSH keys across diverse environments.
Best Practices to Implement SSH Key Management
To maximize security, streamline operations, and achieve regulatory compliance, follow these best practices for SSH key management:
- Centralize Key Management: Implement a centralized system for managing SSH keys to gain visibility, simplify administration, and enhance control.
- Automate Key Lifecycle: Automate key generation, distribution, rotation, and revocation to streamline processes and reduce manual effort.
- Enforce Strong Access Controls: Utilize role-based access control (RBAC) to restrict key access based on user roles and responsibilities.
- Protect Private Keys: Secure private keys using strong passwords, hardware security modules (HSMs), or other secure storage mechanisms.
- Implement Key Rotation: Regularly rotate SSH keys to limit the impact of potential key compromises.
- Monitor Key Usage: Implement monitoring and auditing to detect unusual activity, unauthorized access attempts, or policy violations.
- Educate Users: Train users on the importance of SSH key security and the best practices for managing keys. This reduces the risk of human error or phishing attacks.
- Establish a Key Revocation Process: Have a clear process for revoking compromised or unnecessary keys to ensure the rapid removal of compromised keys.
- Maintain Regular Audits: Conduct regular audits to ensure compliance and identify any vulnerabilities in the key management process.
Effective SSH key management is critical for protecting your infrastructure. Failing to do so leaves your systems vulnerable to attack. By implementing the best practices mentioned above, you can strengthen your security posture, streamline operations, and meet regulatory requirements.
SSH key management should be a core component of your access and IT risk management programs. Many organizations, however, lack a formal SSH key management operations function. This often places the responsibility on individual administrators, which can be a far from ideal situation. Organizations that implement SSH key management and security policies and practices as a fundamental part of their IT and security programs are the most successful at protecting their digital assets.


Detail Author:
- Name : Dahlia Macejkovic I
- Username : drew32
- Email : kadin95@hotmail.com
- Birthdate : 1980-07-30
- Address : 254 Percival Hills Jalynborough, AR 03719-9757
- Phone : (878) 329-1985
- Company : Moen-Erdman
- Job : Bus Driver
- Bio : Omnis aut iste numquam placeat asperiores aut. Quod rem vitae iste. Quasi qui vitae quidem tempora ipsam.
Socials
linkedin:
- url : https://linkedin.com/in/brock_stoltenberg
- username : brock_stoltenberg
- bio : Officia culpa magnam qui error.
- followers : 3888
- following : 566
tiktok:
- url : https://tiktok.com/@brockstoltenberg
- username : brockstoltenberg
- bio : Enim consequatur ut dolores voluptate. Quaerat tempora mollitia aut id vel.
- followers : 4001
- following : 2894
twitter:
- url : https://twitter.com/stoltenberg2021
- username : stoltenberg2021
- bio : Est mollitia necessitatibus nihil aut delectus. Tempore expedita repellendus dolores unde et doloremque. Voluptatem consequatur et minima quia.
- followers : 3996
- following : 269